14 Days To A Better arnobbd
5 helppoa tapaa muuttaa spins menestykseen
June 21, 2023Top 3 Ways To Buy A Used Virtual Slot Machines
June 24, 2023Before You Connect a New Computer to the Internet
Linked regularities in the development and evolution of mammalian brains. Once it gathers all the necessary information, it will establish the link between them and route the data to the receiver from the sender’s end. An Internet in Your Head: A New Paradigm for How the Brain Works. Adaptive resonance among topographically organized arrays leads to a dynamic system trajectory that may 1 land in a local minimum, 2 diverge and dissipate, or 3 even lead to a destructive positive feedback loop. The door remains unlocked until the door has been opened or until the set time has been reached. If using an Apple Mac with the virtualization software “Parallels”, issues with modifier keys SHIFT, CTRL and ALT are known. The switchrelies on its Layer 3 capabilities to provide this basic routing betweenVLANs. While LAN, WAN and MAN all are networking technologies, there are some distinct differences in terms of technologies, geographical sizes and management responsibilities. It’s impossible with the current setup, Larry. TCP is the other half of TCP/IP and arranges packets in order so IP can deliver them. 06 Explain features of an application delivery controller. It also updates the router table with new addresses not already in the table. Need to connect devices wirelessly: Wireless connectivity has become a necessity. VLAN or Virtual Local Area Network creates multiple smaller broadcast domains over a single Ethernet network. The first four nodes were designated as a testbed for developing and debugging the 1822 protocol, which was a major undertaking. SAN is a conglomeration of networks designed for high speed interconnection in server server mode. Artwork: The main contents of an Ethernet frame are thepreamble initial “handshaking” information to let the sender and receiver synchronize, the receiver’s and sender’s MAC addresses,the type and length of data, the data itself, and a checksum at the end to makesure everything has been transmitted properly. Typically, LANs are privately owned and managed. En/computerbasics/getting started with the internet/content/. In the visual cortex, dynamic SA coalitions may represent a single star on a dark night, a coffee cup on a nearby table, a simple event such as a cup falling off a table, and the textured surfaces of visual objects. This WLAN type is usually preferred for most regular wireless network usage. Knowledge of creating and maintaining case logs and generated case reports. Historically, these networks are broken down into topologies, used for connecting computers.

Question
It is a good practice to automate responses to attacks, including blocking IP addresses, terminating connections, and gathering additional information about attacks. Not all network media types have the Why is the operation of cable networks necessary in the office? same characteristics or are appropriate for the same purpose. Typical effects of congestion include queueing delay, packet loss or the blocking of new connections. It will clearly hiccup on the particular router hop that is causing the problem. Mobile hotspot is a common feature on smartphones with both tethered and untethered connections. NIC card is a layer 2 device which means that it works on both the physical and data link layers of the network model. Will pass this along. The primary difference between LAN and MAN is the size of area and distance they cover. The goal of presentation graphics is to provideinformation in a graphical form that helps end users and mangers understand businessproposals and performance and make better decisions about them. However, the future. The data transmissionspeed of LANs is much higher than in other types of networks. 11 compliant implementations.
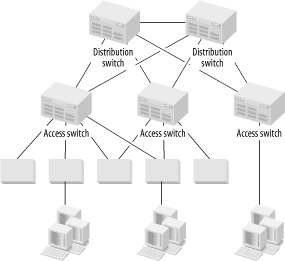
Advantages of LAN
Students may rely on WANs to access library databases or conduct university research. Network interface layer. In this activity you will learn the essentials of using Packet Tracer. One such choice is a cybersecurity boot camp program. Pearson uses this information for system administration and to identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents, appropriately scale computing resources and otherwise support and deliver this site and its services. Most bankers are familiar with the rigid standards required by core providers when you are running out of their service bureau. Fast connectivity has also become available to these devices. 6%, as per IDC reports. This interface can enable communications between enterprise applications and embedded building systems as well as between two embedded building systems.

Layer 1: Physical layer
The second one was that certain secure pages login/PW just would not work at all. Devices will only operate at a limited distance from an access point, with the distance largely determined by the standard used. The connectomics of brain disorders. We compiled the list based on expert opinion, and user experience. Connect the computer following the setup process with the necessary details. Maybe you’re lucky and have a fiber connection. Broadcast A message that is sent to all clients on a network. The four numbers in an IP address are called octets, because they each have eight positions when viewed in binary form. If a timely ACK is not received, a driver in thalamus could be triggered to resend the missing message.

Uses Of Metropolitan Area Network:
Modern Gigabit Ethernet standards, for example, are 100x faster than the old 10Mb/s cards and cables that were common in the 80s and are still in use in some areas today. When issues do occur, networking configuration management allows the administrator to quickly correct the problem by modifying the configuration or adding more network resources. In a LAN, working with a file server, all application running in a workstation may request for a file with involving the local operating system. 02 Explain the function and purpose of a router, of a firewall and of a switch. Having a Cisco wireless network makes it easy to bring new devices online and provides flexible support to mobile workers. Get the Latest Tech News Delivered Every Day. In built templates specific to your search will appear on the screen. Additional APs are used to allow access to more wireless clients and to expand the range of the wireless network. Big data technology provides sufficient storage and rapid searching for massive asset information data and enables multiple applications. It transmits data in the form of light. However, ethernet switches cost $10 $100 depending on quality and features. Yet, the growing global shortage of qualified cybersecurity professionals has forced organizations to reassess what’s truly important for a candidate to succeed in the role, recognizing that candidates may have obtained their skills through alternative pathways or self teaching. Another example of virtual networking is a virtual local area network VLAN. If you’re looking for ways to maximise the potential of your home network, especially if you work from home or have multiple laptops or desktop computers in the household, you may want to consider setting up a LAN. They have the latest driver updates to get rid of network identification issues. Organizations should consider data center tiers of colocation providers or for their own data centers based on their uptime needs. Besides that, there are eight octets rather than four, and the address is 128 bit rather than 32 bit. Implementation Points: Internal wireless user perimeter. In this article on ‘Types of Networks,’ we will look into different types of networks and some of their important features. So, it’s obvious that we would never want our guest network traffic or host on the guest network to be able to reach the host and our finance department, right. Real time monitoring of network activity is essential to the security of a network. Fill in your details below or click an icon to log in. In order for a company or an individual to use a computing device with confidence, they must first be assured that the device is not compromised in any way and that all communications will be secure. Once a connection is established between the finance branch of the parentorganization and the library, a correct record of expenditure can be obtainedwithout delay, which will enable the proper utilization of funds. When it comes to speed of information and file exchange, LANs trump all the others. In this topic, we discuss the most prominent wireless PAN technology: Bluetooth, which we introduce in next topic. Step 3: Next, type the command ipconfig/release and press Enter. Typically, Steam checks for updates after logging in, but in case it doesn’t, manually updating is quick and easy. For example, in an office with multiple departments, such as accounting, IT support, and administration, each department’s computers could be logically connected to the same switch but segmented to behave as if they are separate. Wide Area Network or WAN3.

See Also
WAN provides a slow Internet connection. There are different types of ports available in a computer network. For example, one might signal “ready to send” and wait for the other to signal “ready to receive. The Internet Assigned Numbers Authority IANA has assigned port numbers to commonly used services like SSH, FTP, HTTP, HTTPS, and others. When it was defined, the “Automatic metric” checkbox was used. The syntax of this command is. PBB TE allows for immense service scalability—up to 16 million VLANs across a WAN—while also allowing complete segregation of various enterprise VLANs. Supportive evidence has been reported by Doesburg et al. Wi Fi uses radio waves in the 2. Law firms have a lot of information to protect. Other companies, such as IBM, adopted the token passing scheme to battle Ethernet for LAN supremacy throughout the ’80s. Service Set Identifier SSID broadcast is what makes your WiFi network visible to your network adapter. Thank you for making the recent VIRTUAL and IN PERSON events a success. Just kidding, we still have nodes, but Layer 5 doesn’t need to retain the concept of a node because that’s been abstracted out taken care of by previous layers. Wireless networking has become increasingly popular, especially for portable and handheld devices. You can enable NordVPN’s Meshnet feature on that computer, and on a device you carry with you a laptop or a smartphone, for example. Ethernet and Wi Fi are the two primary ways to enable LAN connections. But in general computer networks are divided into three general groups based on size. In the dialog, enter the IP address of the gateway and select the routing metric that you want to assign to this route. Now create the VLANs and the IRB. Still, WLANs allow you to move around conveniently with laptops and smartphones in the area. Select the ‘Net Banking’ option and the choose the bank account from which you want to make the payment. Online only banks may not provide direct ATM access but will make provisions for customers to use ATMs at other banks and retail stores. The function of Local Area Networks is to link computers together and provide shared access to printers, files, and other services. Thanks very much its very helpful.

What Do Tech Companies Want in Cloud Experts?
Connect other devices: After finishing the installation, connect other devices with the network. Which of the following is not a characteristic of a weak password. Not only is this connection highly convenient, you also didn’t have to use your smartphone’s data. Below is a list of some of the disadvantages of the network layer. COM top level domain must be unique. In addition to computers, routers or servers, peripheral devices such as printers or IP cameras also form part of the network. On rare occasions it is necessary to send out a strictly service related announcement. D desktop thin clients;. But not in Silicon Valley, where the 11th meeting was held for the ETSI Network Functions Virtualisation Industry Specification Group NFV ISG. 2 can also be served via the NGMN supernetwork. In the US the Sprint was an early adopter of fibre optic rings that routed IP packets on the MAN backbone. Bluetooth is even more improvised: nearby devices detect one another, connect together when you give them permission,and form a generally short lived computer network—before going their separate ways. A VPN establishes an encrypted channel that keeps a user’s identity and access credentials, as well as any data transferred, inaccessible to hackers.

FOLLOW US
Disadvantages of Client Server Network Operating SystemsThe disadvantages of Client Server Network Operating System are as follows. To configure a VLAN with IRB support, include the followingstatements. For example, one subnet may specify a different router than the rest of the subnets, or one host may use a different router than the other hosts in a subnet. It will support the services to maintain network elements and network performance monitoring and management. Pearson does not rent or sell personal information in exchange for any payment of money. In the examples above, I assumed this would be the case. The physical or geographic locations of network nodes and links generally have relatively little effect on a network, but the topology of interconnections of a network can significantly affect its throughput and reliability. These types of cloud based services provide businesses with the functionality of a LAN without being tied to a single location; we’ve explored them in another Learning Hub post about cloud services for business. This allows computers to have dedicatedbandwidth on point to point connections to the network and also to runin full duplex mode. The fourth ETSI ISG NFV plenary meeting was held on the 30th October to 1st November 2013, in Sunnyvale, USA, and was kindly hosted by Juniper and co sponsored by IBM. Since it enables employees to access information in seconds, networks save operational time, and subsequently, costs. The objective of a hop is to minimize one of the metrics such as the number of hops required for a particular packet.
Figure 4 17 Ethernet frame with 802 1Q trunking
In the case that all of the cables are plugged in correctly but the error message is still displayed, there are three possible problems. Thus PoE switches offer more flexibility. The first working network, called ARPANET, was created in the late 1960s and was funded by the U. Ethernet network protocol monitors the data transfer over a local area network. This essentially turns the switch into a hub. Engineers usually report both the maximum and average delay, and they divide the delay into several parts. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. DNS is important because it can provide users with information quickly and enable access to remote hosts and resources across the internet. Wireless LANs use the IEEE 802. For analog access, a modem is required. Network administrators can see networks from both physical and logical perspectives. These devices help a network establish communication within the network or outside the network. Dat Typical Path: %windows%system32Com Unique Characteristics: High Entropy Role: Houses Snake’s kernel driver and the driver’s loader. The access networks offer diverse options of technology ranging from DSL to WiMax. Compared to the data transmission speed, LAN is faster than WAN. Wired Personal Area Network: Wired Personal Area Network is created by using the USB. Plugging your computer in directly to the modem is no different than the dial up days, although the World Wide Web is now bigger, darker, and more populated. Select “Internet” → “Internet Settings”. GMT Monday through Friday. D Commercial and Industrial Security Corporation✔. The modem working efficiency and processing is decided by two factors. Security is critical when unprecedented amounts of data are generated, moved, and processed across networks. These systems alert officials and emergency responders with information about traffic flow and incidents. These are the unique IDs under which the PCs can be identified and reached on the network. There are many IEEE specifications related to Ethernet, but one specification that is used extensively in Ethernet networks is VLANs.
Anywhere WorkspaceAccess Any App on Any Device Securely
Click ctrl+F and search for last bind;. Example 2: Token Ring Network. Audio ports are used to connect speakers or other audio output devices with the computer. If the destination node does not receive all of the data, TCP will ask for a retry. The awesome technology at this point was 100Mbps shared Ethernet. Archives Partnership Trust. Residences and offices use wireless connections. @habamax commented on Jun 10, 2020, 7:38 PM GMT+7.
Figure 4 15 Telephone lines and trunks
Our tech experts at United World Telecom can help you identify the best VoIP solution for your business. Depending on the type of cable you use, it might not be able to carry more than 1Gpbs though it might. A range of evidence suggests that phase coupled firing of large numbers of neurons is involved. If it changes, you have correctly set up VLANs, great job. The network packet will be sent only to a very specific broadcast domain, whereas on an LAN it’s available to anyone. Affordable solution to train a team and make them project ready. Radio Transmission wirelesscommunications technology that transmits voice or data over the air using a lowerfrequency band than microwaves. It may also be a larger area, such as an entire office building containing hundreds or thousands of devices. Ethernet was evolved from a protocol called ALOHA. For more details on setting up a Cisco IE switch, refer to the Cisco IE switch installation guides. MANs mostly use fiber optic technology to connect multiple LANs. One of the introduced abstract NFV objects is the Managed Container Infrastructure Object MCIO, an object managed and exposed by the CISM, characterized by the desired and actual state of a containerized workload. The cost of setting up MAN networks is relatively high and only affordable for companies and organizations. REX does not unlock door – Select if the REX signal does not influence door opening for example for doors with mechanical handles or push bars. Peer to peer networks are typically limited to homes and small businesses such as restaurants or coffee shops. This means that the overlay and the physical IP network are decoupled and you can make changes to either network without making any changes to the other. LAN networking requires cables, switches, routers and other components that let users connect to internal servers, websites and other LANs that belong to the same wide area network WAN. As you can imagine, all traffic of the 2nd building and the outside world has to go through the 1st building, and the mailing service for those in the 2nd building can be complicated they have to deal with two mailrooms. When one device sends data to another, the data includes a ‘header’ that includes the IP address of the sending device and the IP address of the destination device. Once traffic crosses a router and engages Layer 3 IP related functions, it is not considered to be on the same LAN, even if everything stays in the same building or floor. The two must have different local IP addresses. If not, you can review our lesson on How to Set Up a Wi Fi Network to learn more. Two users a half world apart with workstations equipped with microphones and a webcams might teleconference in real time. Please don’t hesitate to reach out to our team with questions on positions or for more information about our company. In such structures, clients and servers exchange certificates which are issued and verified by a trusted third party called a certificate authority CA. A specific network port is required to transmit or receive data from network devices. Networking devices are the hardware devices used to connect mobiles, computers, printers, and other electronic devices to a network. Read more about Computer Networks. And at higher levels object and face identity, semantic category, and the like.
